The man-in-the-middle (MITM) is a cyber attack method used by threat actors to invisibly intercept a user’s online activity. It could be an email conversation between two colleagues or a user’s interaction with a website or web application.
By secretly intervening in the user’s activity, the cyber criminal can manipulate conversations. They can also gain full visibility of anything the user does including entering passwords and financial details in real time.
It is estimated that 35% of cyber attacks involve man-in-the-middle activity.
How does a man-in-the-middle attack work?
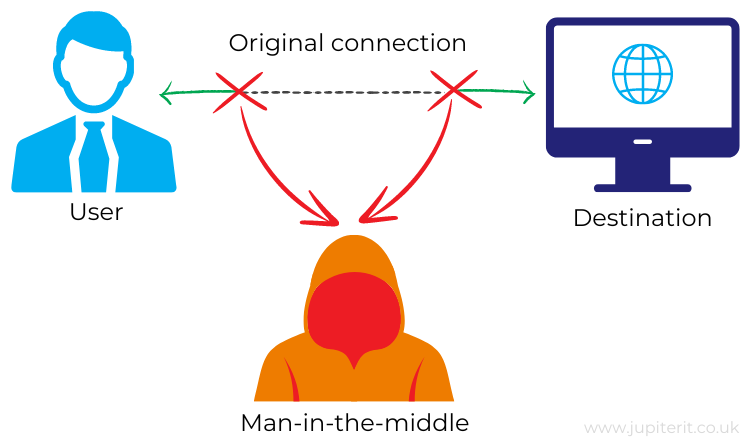
In simple terms, the hacker cuts off the user’s original communication connection and places themselves as the host of the interaction. A cyber criminal can achieve this in several ways, but the easiest and most common method is to plant malicious free WiFi spots in public areas.
Once in position, the hacker can capture data and manipulate anything that comes their way.
One of the most famous cases of a man-in-the-middle attack was in 2015 when the European Union Agency for Law Enforcement stopped a group of threat actors who were intercepting business/client communications across Europe to instruct money transfers to illegitimate bank accounts.
What types of man-in-the-middle attacks are there?
There are many ways for a cyber criminal to execute a man-in-the-middle attack. These are some of the most common:
Network spoofing – A form of cybersquatting, hackers can alter IP addresses and domain names to trick users into believing they are interacting with a legitimate source or visiting a legitimate website whilst the user is actually interacting with the hacker.
HTTP spoofing – The rule goes, that if a website URL starts HTTPS, it’s safe. But in the case of HTTP spoofing, the user is redirected to an unsecure site during their browsing session without knowledge. From this point forward, the hacker has sight of everything they do.
Email hijacking – This type of MITM attack takes control of emails to manipulate a user’s actions. The hacker may intercept an email conversation between colleagues and alter the content to request important passwords. This type of MITM has also been used to take control of emails sent from banks and amend them to prompt customers to pay bills or access their accounts via malicious links.
WiFi evesdropping – Hackers use the temptation of free public WiFi to attract users to connect to fake WiFi hotspots. These malicious connections are often set up with names similar to nearby businesses, so it’s always worth checking with the establishment if the connection is in fact theirs.
How can you protect against man-in-the-middle attacks?
#1. Check your network is secure
There are a couple of ways you can do this: Always make sure the URL you are visiting begins with HTTPS – not just HTTP. If while browsing you feel something has changed – perhaps the site pauses momentarily or reloads itself – check the URL is still showing HTTPS. If your browser displays a padlock ahead of the URL, this is also a good sign the website is safe.
We recommend you avoid using unsecured public WiFi wherever possible. These are a major target for hackers and are highly susceptible to MITM attacks.
#2. Be aware of phishing emails
Phishing emails are growing more and more sophisticated and often look like they are coming from a legitimate source. If you receive an email from your bank or any other financial institution, never access your account via the link provided. Go directly to their website or give them a call.
More ways to spot a phishing attack.
#3. Use a VPN
With a virtual private network (VPN) your connection and all data transfers are encrypted. As a result, even if a hacker manages to gain access to the network, they won’t be able to decipher any information they see.
We’re the cyber security experts
As the risk of cyber crime grows, we know that cyber security has never been more important for businesses.
At Jupiter IT, we offer expert cyber security and IT support in Hull and the surrounding areas. Every client benefits from a free cyber security audit and free cyber security awareness training tailored to their employees needs.







